Basic security for your Mikrotik RouterOS Cloud Router
Started a Mikrotik RouterOS on CloudBalkan? First thing to do – you shall secure your new cloud router as soon as possible. In this article we’ll talk about the basic security measures you can immediately apply to your routers.
There are five simple protection mechanisms you need to take in mind when you start a new Cloud Router:
- Security updates
- Management interfaces security
- Firewall protection
- Users management
- Logging
Security Updates
Yes, although this may sound quite trivial, keeping your RouterOS up to date is definately one of the top 5 measueres you shall take. And as it is the simplest one we recommend to start with it, before you did any configuration on your router. To update your Cloud Router, login to the web interface and go to the ‘System > Packages’ menu.

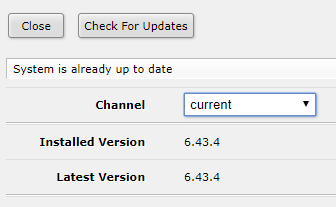
Click the ‘Check For Updates’ button to check for a newer version. You will see the current version and any updates if available. If there are updates available, you’ll be able to click the ‘Downloa & Install’ button:
![]()
By clicking on the ‘Download & Install’ button your Cloud Router will download the updates, restart and install the newer version. It takes less than a minute.
Management interfaces
A very good practice is to protect your management interface from the very beginning. This includes two steps – first disabling unnecessary/insecure services and second, highly recommended – changing the active services default ports.
Disabling some services is necessary bacause RouterOS comes with some common, but pretty insecure services enabled. To see and manage those services, you can go to the ‘IP > Services’ menu:
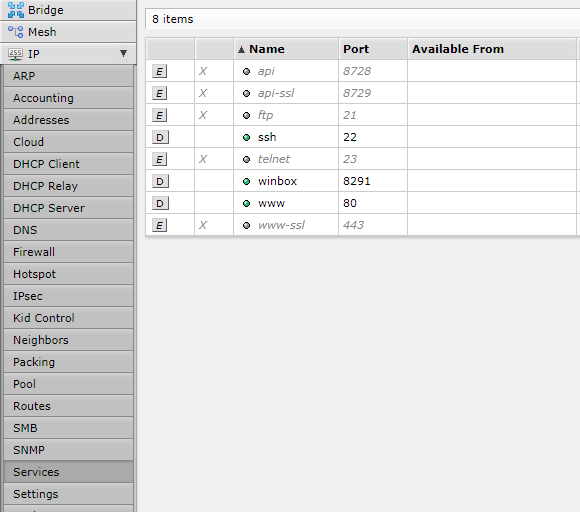
We highly recommend disabling protocols like FTP and Telnet. If you don’t plan to use the API or Winbox, you can disable those as well. The second part of securing the management interfaces is to change the default ports. We always recommend this as it is a simple step that save a lot of potential problems. Using for example different ports for the SSH and HTTP, makes it a lot harder for bots and botnets to detect the runinng service on your device.
Firewall
As a very basic security measure we recommend the use of some simple firewall rules, restricting the access to your router. We’ll firewall only the ‘input’ chain which means connection destined to the router itself. If you don’t really need a free access from the world to your router you can also limit the access to only white listed IP addresses as well.
We’ll do two simple rules:
Allow your IP addresses to access the routers management interfaces:
/ip firewall filter
add action=accept chain=input dst-port=22,80,8291 protocol=tcp src-address=your.ip.addr.ess
Deny access from the rest of the world:
/ip firewall filter
add action=drop chain=input connection-state=!established,related dst-port=22,80,8291 protocol=tcp
Where here ports 22, 80 and 8291 allow acccess to SSH, HTTP and the Winbox protocols, only from the specified ‘your.ip.addr.ess’.
If you actually skip the ‘dst-port’ you can limit all types of traffic to only your IP address or network range.
User management
In terms of user management, our basic security steps recommend the simple rules – change the default username and use strong passwords. To manage users on your RouterOS, go to the ‘System > Users’ menu.
Logging
Final but yet pretty important step is to get you known with the Mikrotik RouterOS logging facility. It is enabled by default and it logs every unsuccessful attempt for authentication on your router. Keep in mind that monitoring the logs is always an important part of the good security. Keep an eye on it and use the other security mechanisms to limit and prevent any potential attack attempts.
If you leave your router unprotected you’ll pretty soon start to see log records like the ones below, attempting to access your poor devices.
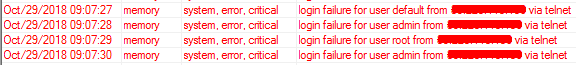
This short list is intended just to put your attention on the very basics of Cloud Routers security. Track the CloudBalkan blog and the #security channel for more in deep articles on network security.